Do you remember the new version of the Hello Peppa botnet? At the end of 2018, it was welcomed into 2019 slightly early, and the January botnet started to spread. Well, it wouldn’t be funny, if the botnet would still send the „J4nur4ry” in the Post Data when we are already over January…
So, here is the February botnet!
Despite the January botnet, this one was accurate and started on 1st February. The pike was on the next day, as you can see it from the chart below.
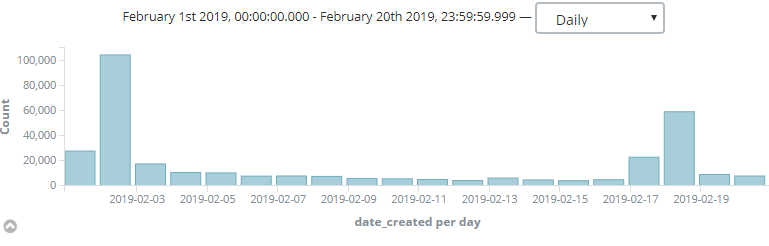
After that, it looked like it moved back, but on 17th Feb there was another pike. Let’s look closely to one of the requests sent by this botnet:
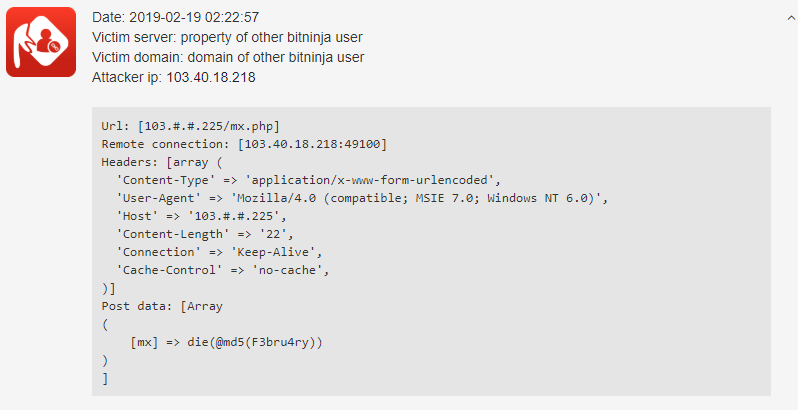
The only difference between this well-known botnet is in the Post Data. Now, as it’s February, we can see the F3bru4ry there and now they could spell it well. (Last time they had a typo in the J4nur4ry.) Other specifics of the botnet didn’t change.
- Checks backdoors which have remain from a previous infection.
- Uses the Mozilla/5.0 User Agent
- The most targeted URLs are:
| /7788.php |
| /8899.php |
| /9678.php |
| /conflg.php |
| /db.init.php |
| /db__.init.php |
| /db_session.init.php |
| /mx.php |
| /qq.php |
| /s.php |
| /sheep.php |
| /w.php |
| /wc.php |
| /wshell.php |
| /wuwu11.php |
| /xshell.php |
| /xw.php |
| /xx.php |
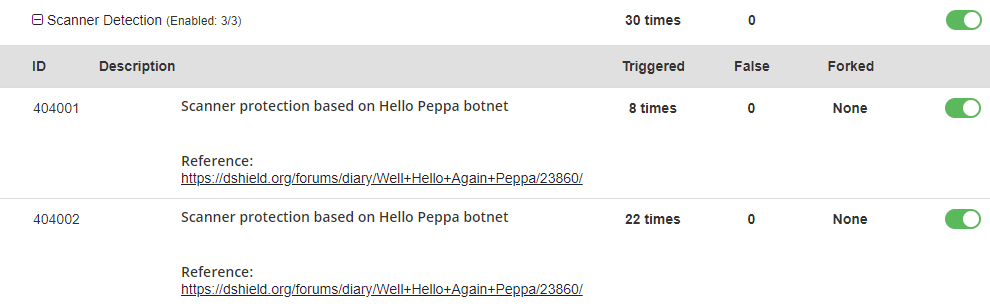
Protection against the February botnet
The 404001 and 404002 WAF rules, which protects you against the Hello Peppa and the January botnet will work the same way against the February botnet too, so with BitNinja Pro, you don’t need to worry about getting hacked by this funny botnet.
What do you think? Will it be a habit to change this botnet from month to month? We’ll get the answer in March. 😉
Stay safe dear Ninja!


