Content Management Systems (CMS) are highly vulnerable to zero-day attacks recently. Lately, the Drupal was picked on by the hackers. Now the ModX CMS is in the target.
CVE-2018-1000207: The new MODX vulnerability
Two critical vulnerabilities have been found in MODX Revolution <= 2.6.4 in the past few days. Exploiting it, the hackers can remote code execution so they can compromise the website and modify (spoil/delete) the files and directories. This vulnerability has already got a CVE number: CVE-2018- 1000207.
With a single web request, the attacker can create a custom file name and content through a phpthumb class. Why is it possible? In MODX Revolution 2.6.4 and in the previous versions, the parameters of the user filtering have an incorrect access control vulnerability.
Zero-day botnet starts spreading around
At 26th July at 6 PM, the flow has been started according to our data. This botnet is really aggressive, as, in the first 6 hours, we detected almost 13.000 attacks!
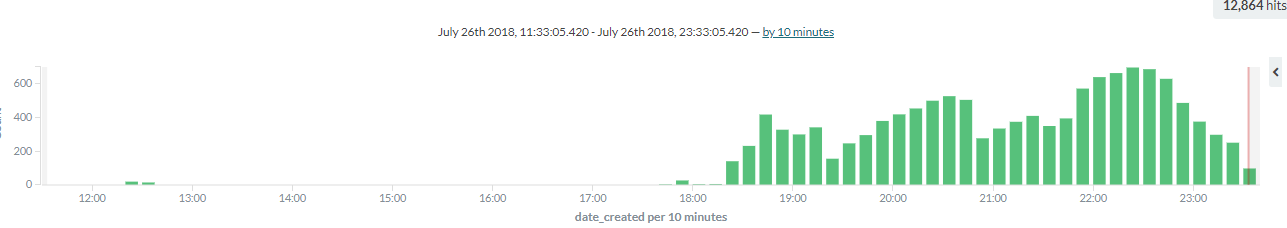
The peak was at 22 PM on the same day and since then, the number of attacks started to decrease, but don’t believe that’s it’s over.
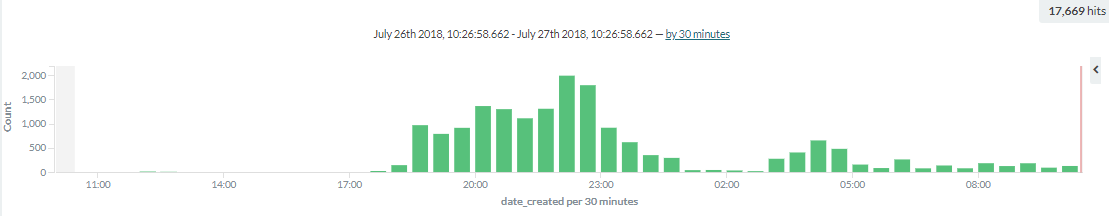
Analyzing the incidents
Here is a screenshot from the BitNinja Dashboard about one of the attacker IP:
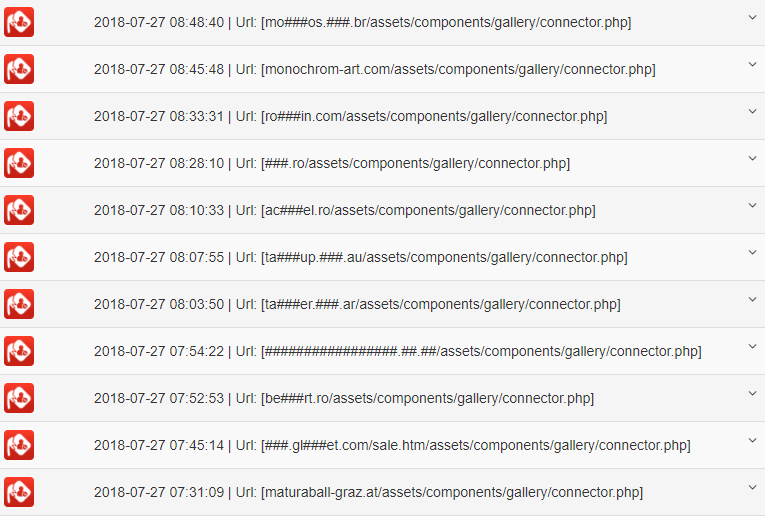
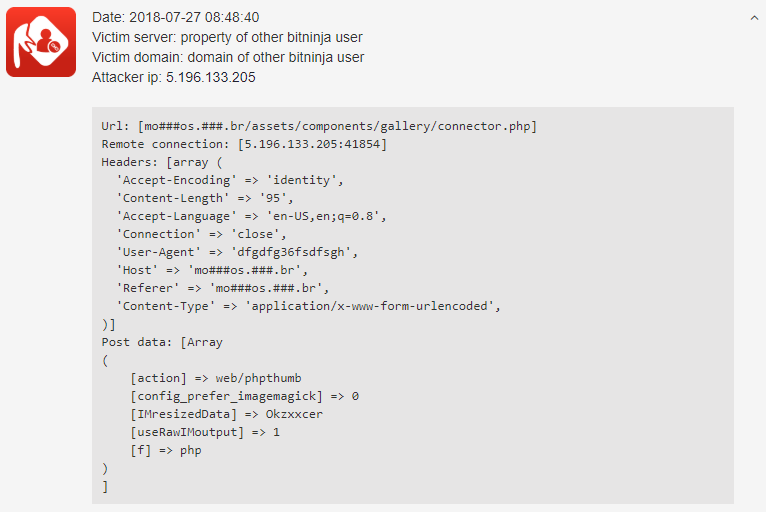
Looking through these logs, we are sure that you could find the pattern by yourself. The bot is scanning the /assets/components/gallery/connector.php continuously. Let’s investigate a log from a little bit closer:
Attacking countries
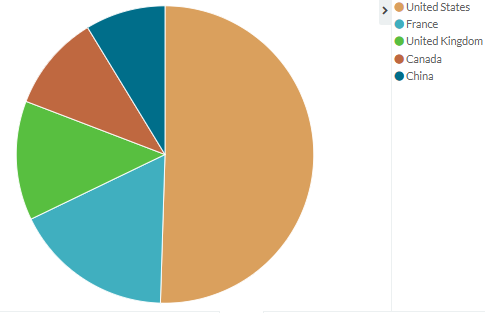
In the first 17 hours, 29% of the attacks came from the US. The Top5 attacking countries are the following:
| 1. | United States |
| 2. | France |
| 3. | United Kingdom |
| 4. | Canada |
| 5. | China |
Examining only these 5 countries, the US is responsible for 50% of the attacks as you can see from the graph below.
How to be protected against MODX Revolution <= 2.6.4 Remote Code Execution?
BitNinja is always up-to-date for the zero-day attacks and vulnerabilities. We’ve implemented a brand-new development, the Attack Vector Miner for your safety. We are not only detecting the new botnets but also offering an direct protection against them.
Don’t let CVE-2018-1000207 compromising your servers! With BitNinja Pro, you only have to do is enable the 403001 WAF rule on the Dashboard.
Need help with it? Have questions? Leave us a comment!
Stay safe dear Fellow Ninja!




