Our Hungarian web hosting partner, web-server.hu had ZERO website infections – since enabling BitNinja’s new WAF 2.0 module. We caught up with the lead sysadmin to talk to him about his experience with BitNinja.
What has been your experience with BitNinja overall?
“Before we began using BitNinja, we had to fight daily battles with hackers. Infected WordPress, Joomla, Drupal and other accounts were the most commonly affected platforms. Because of the continuous battle with infections and DoS attacks, we hardly had any time left for servers and for development. Since we started using BitNinja, the overall number of these incidents has dropped substantially. We’ve had no further DoS attacks and only a couple infected websites – per week. Cleaning the infections was super easy as the Malware Detection Daily Reports – gave us all the necessary details to work with.”
What is your experience with the WAF 2.0 module in particular?
“We were alpha testing the new BitNinja WAF 2.0 module and found it to be a very great experience. At the beginning, there were some performance issues, but the dev guys at BitNinja have since, fixed them. The number of infections was reduced, and even with 1-2 backdoor uploads per week, we had no major infections. Finally, we had a tool to fight with. Our sysadmins then tweaked the rules and set up a stricter ruleset for the accounts in danger.”
How did you manage to have zero infections?
“Thanks to the rule tweaks, and a couple of new rules auto-deployed by BitNinja, we had zero infections over the past 8 days. No backdoor uploads, no webshells, nothing at all from the hackers. We are very satisfied with these results and hope, we can keep this hacker-free period for a long-long time!”
Maybe hackers stopped attacking, or there was some major law enforcement action taken to lessen the attacks?
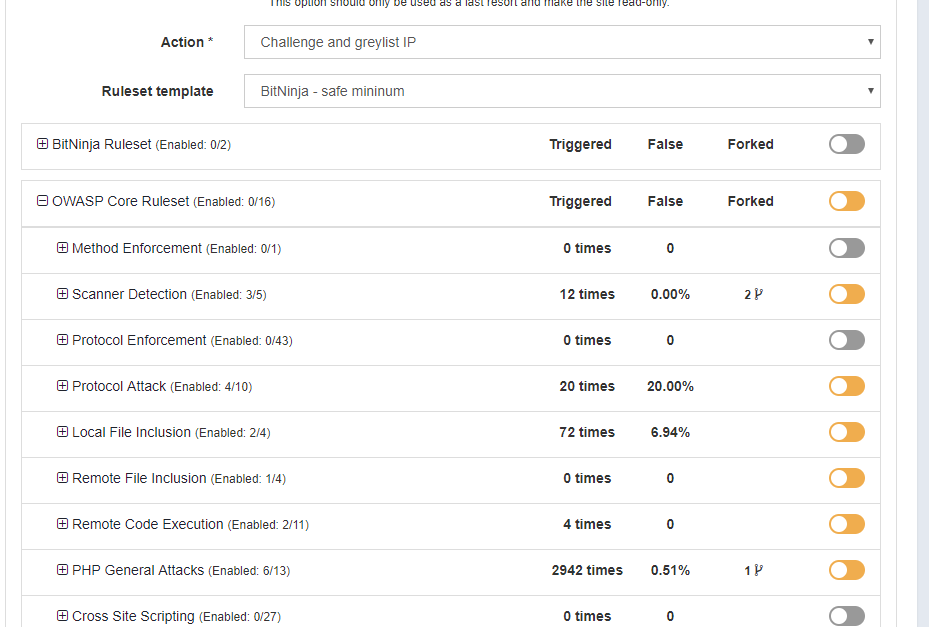
“I am absolutely sure that the WAF 2.0 keeps blocking the attacks. In the last 7 days, it blocked more than 3,000 attacks, according to the https://admin.bitninja.io/ipmanager/analyze report. We use WAF 2.0 in active protection mode, so these 3,000 attack attempts are more or less unique attacks, as the IP is greylisted after a WAF incident – so further attempts will not count as WAF incidents.”
Were there any user complaints?
“There were a couple of requests from users connected to the WAF – however, it was easy to set up a domain pattern and disable problematic rules in these situations. We have also trained our support staff on how to configure the WAF so they can do it right away – when the request comes in.”
Which rules were the most beneficial?
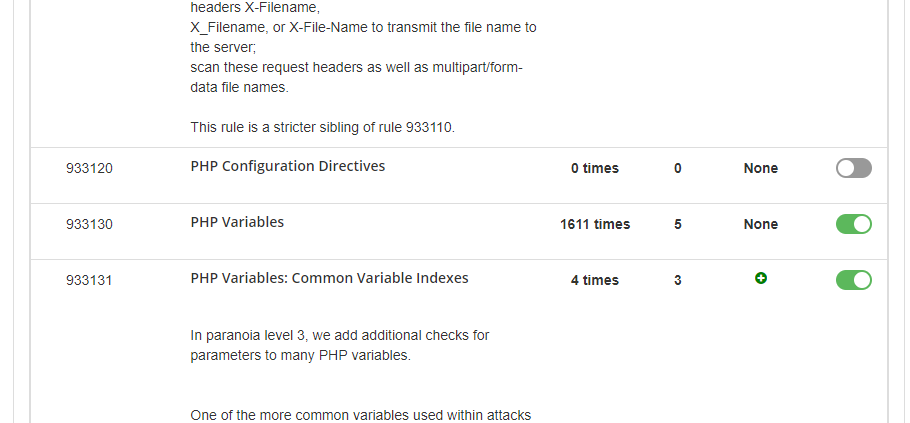
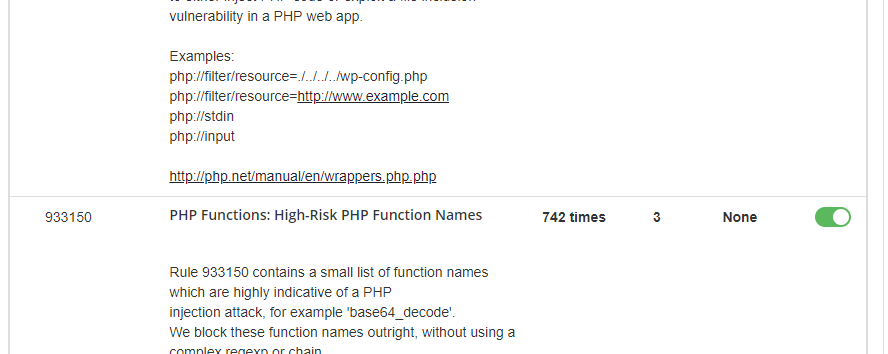
“We use the BitNinja Safe Minimum rule template as the default domain pattern (*/*) and use both the medium and strict templates for a couple of domains. Looking at the results "PHP variables", "PHP Object Injections" and „PHP Functions: High-Risk PHP Function Names” has a very high catch rate with extremely low false positives.”
Try the new WAF 2.0 too, and achieve these amazing results yourself!
It's a real hacker-killer in terms of WordPress -, Drupal -, Joomla hacks, data theft, file injections and many more –not to mention its fine-tuning options where you have the opportunity to configure the protection to your needs - with no false positives.
















