On 12th May 2017, the biggest cyber attack of recent times has happened and the threat is still present. Started from Europe and within a couple of hours has grown into a worldwide virus. The crisis has been caused by the WannaCry ransomware and its variants. The virus locks the infected computer and informs the users with a message onscreen. They can only continue to use the PC after paying $300 or $600 in BitCoins. According to the experts, the device used during the attack was developed by the renown Shadow Brokers hacker group.
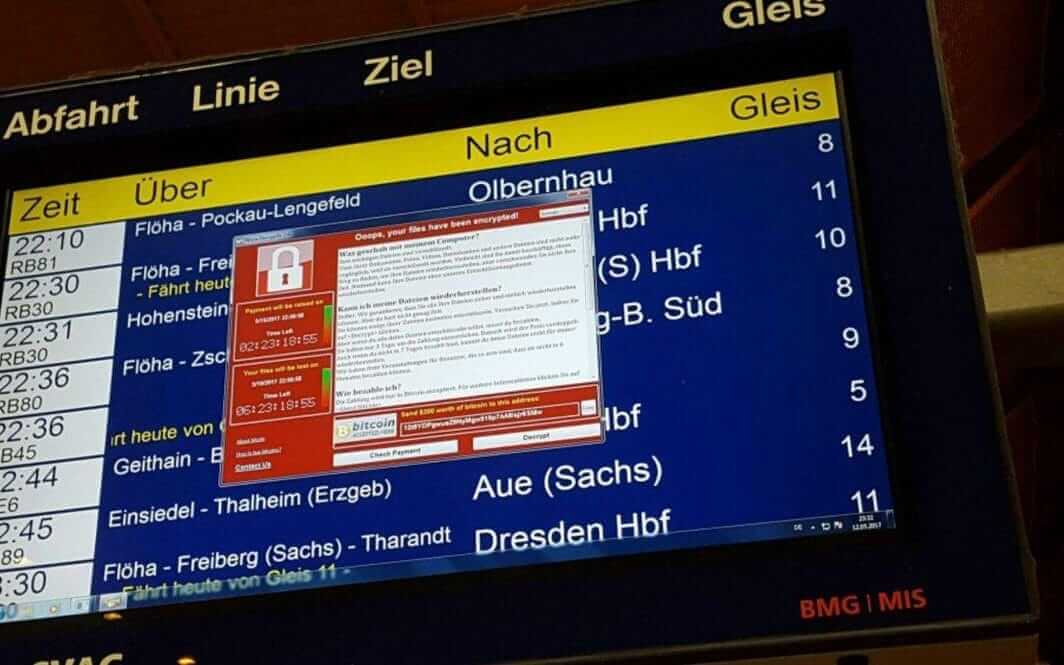
The ransomware might have been combined with the Eternal Blue, which was developed by the NSA and later was stolen, as a result, the WannaCry is able to spread independently. It is able to initiate remote code execution in Windows.
According to the experts of Avast Security, Russia, Ukraine, and Taiwan were the main targets of the massive attack, although the biggest IT systems affected were in the property of the English and Scottish National Health Service. Concrete data was not shared by the NHS Digital, who is responsible for the IT systems, they only hinted that ”several” institutes are affected.
Moreover, there is no evidence of data loss. However, due to the attack the Medical Institutes, the program has been modified, they had to interrupt their normal workflow, for instance, they postponed operations and stopped tests. Where it was necessary and in the case of urgent tasks, they analyzed and processed data manually.
The attack affected the Spanish Telefónica, the machines of the German Deutsche Bahn Railway company, the Hungarian Telenor among others. Fortunately, they noticed the attack just in time, so stopped their systems and no serious damage was caused.
Combating WannaCry
A 22-year-old Brit IT specialist accidentally found out how to stop the ransomware. He realized that for the further expantion of the virus along domain address has to stay inactive. According to The Register, this is the: iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com domain.
So he registered it and the pace of the expantion started to gradually decrease. Darien Huss, a security specialist from Proofpoint, argued it is possible that this option was built into the virus intentionally, so when the creators feel like it, they can stop the event anytime.
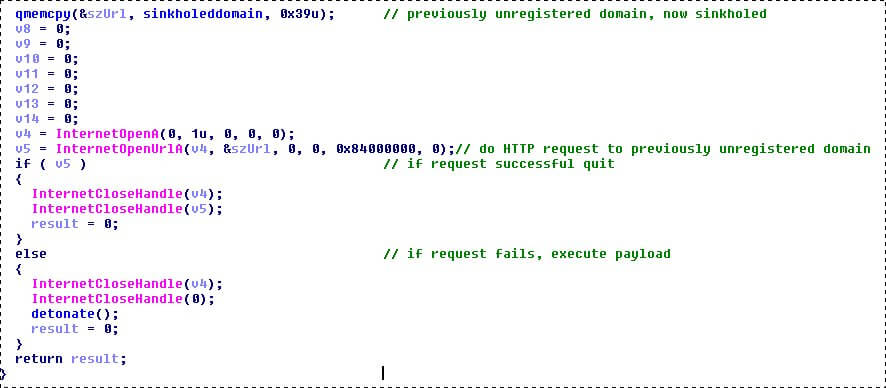
You can track the spreading of the WannaCry.
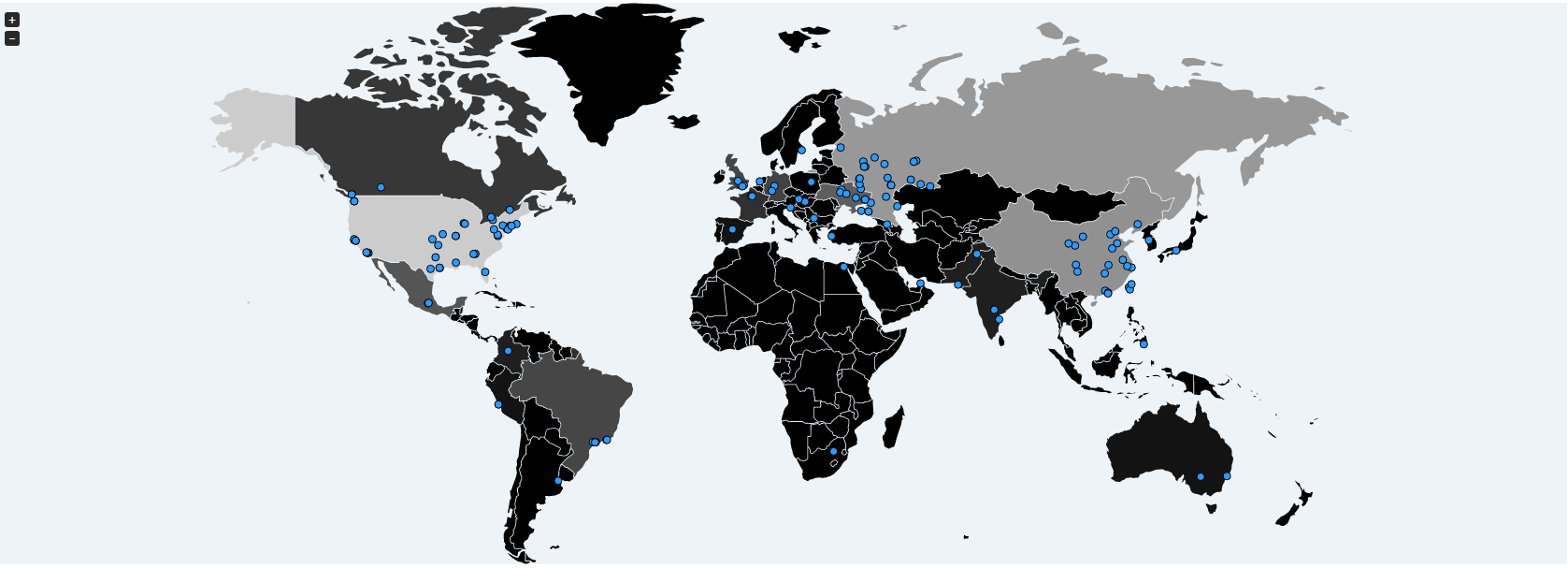
The NSA’s backdoor to Windows
The vulnerability has been discovered by the American National Security Agency aka The Big Brother and other than discovering it, they wanted to exploit it too for their own purposes. After this came the previously mentioned Shadow Brokers group who stole it from the NSA. They wanted to sell it at the Black Market on an online auction. However, later they decided to make it available to everyone free of charge. On the 8th of April, as a protest against Donald Trump, the newly elected president of the USA, they revealed the password needed for the decryption. Many cyber security experts said that the virus is outdated, thus it is not harmful.
Eternal Blue
"An exploit for MS17-010 written in Python with example shellcode. This is based on the Eternal Blue tool stolen from the NSA, and was developed by infosec biz RiskSense. It reveals that the SMB server bug is the result of a buffer overflow in Microsoft’s code. A 32-bit length is subtracted into a 16-bit length, allowing an attacker to inject more data than they should into the networking service and ultimately hijacking the system. Disabling SMBv1 disables the bug, and is recommended in any case. You should also firewall off SMB ports 139 and 445 from the outside world, and restrict access to the service where possible on internal networks." via TBG Security.
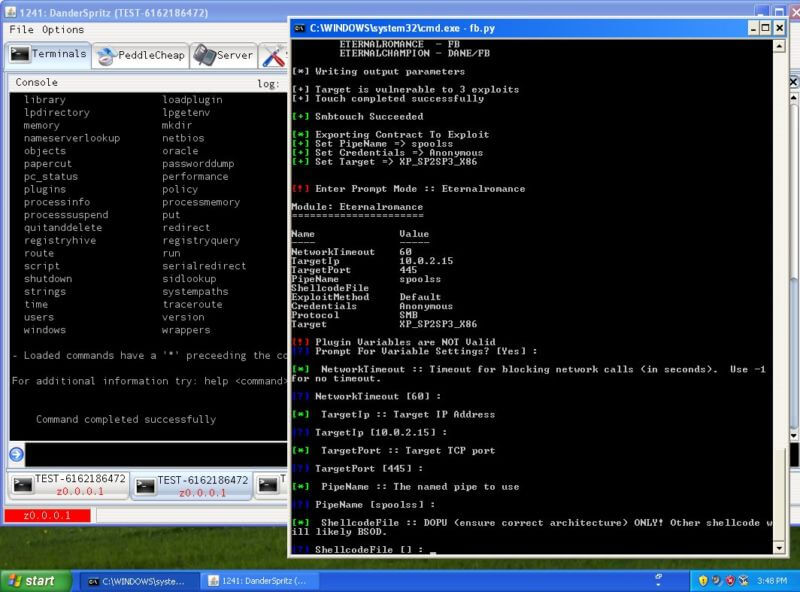
(The picture by arstechnica.com)
Ransoms
Security experts, - in order to follow-up on the ransoms -, created a Twitter account called „actual_ransom”. Here – thanks to a bot- you can watch live as the money flows into the WannCry’s bitcoin purse. Until Tuesday, there have been, 229 successful payments which is around 61,881,24 USD. Paying in BitCoin is not as easy as for example paying on AliExpress, this could be one of the reasons, why there have been these few payments so far.
Theories:
- Microsoft’s plan with this virus was to force people still using Windows XP switching into Windows 10, but thanks a badly written code, they couldn’t keep it in check. This little mistake led to a global problem. To avoid future atrocities, they created an update for the older Operating Systems as well.
- The hackers wanted to show how vulnerable the world is in the 21.century. They were able to get the whole digital world to its knees only in a few hours.
- This attack was aimed directly at the governmental institutions, but because of a flaw in the code, it failed.
- People who are against the modernization initiated the attack in order for the Society to degenerate.
What do you think of this global problem? Do you have your own theory? Share with us. 🙂



