XML-RPC attacks are “trending” nowadays. If you search for “XML-RPC attack” on Google, you can see approximately 380,000 results. Most of the articles deal with XML-RPC attacks on WordPress-based websites.
What is XML-RPC?
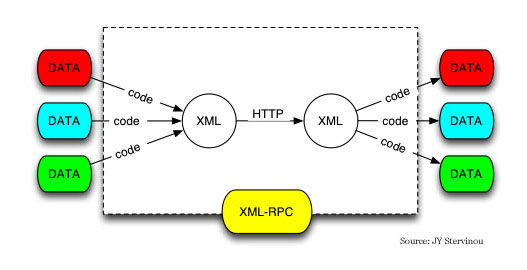
RPC stands for remote procedure call and XML is the abbreviation of Extensible Markup Language. XML is widely used to represent data structures used in web services, and it is markup format that’s both human- and machine-readable.
XML-RPC is a protocol that uses XML to encode its remote procedure calls. It also uses HTTP as a transport mechanism.
The protocol was created by Microsoft in the late 1990’s. XML-RPC works by sending an HTTP request to a server implementing the protocol. Multiple parameters can be passed to the remote method and one return value is returned. The protocol can be used to transport structures or object as input or output parameters.
Why are WordPress XML-RPC attacks so frequent?
Last week while I was checking the logs of our running services I encountered a massive XML-RPC brute force attempt. There were lines crawling all over the logs containing the following information:
xx.xxx.xxx.xxx - - [ +0000] "POST /xmlrpc.php HTTP/1.0" 200 181 "-" "-"
The IP address is obfuscated on purpose.
It is an attack we frequently encounter in the server security business.
The popular CMS WordPress uses an XML-RPC interface. XML-RPC has a system.multicall method which can be used to utilize a brute force attempt without sending a lot of requests. If the hacker send e.g. 500 single calls to guess the password for a WordPress website, it can be easily stopped. But if the brute force password guessing can be made in a single request (by using the XML-RPC protocol), it becomes harder to stop these attacks.
It basically means that hundreds of passwords can be sent during a single HTTP request.
Some WordPress plugins are using the file xmlrpc.php - so blocking the file is not always possible - but it is generally advised to block all access to this file if none of your plugins are using it.
How do we provide protection?
When one of the servers protected by BitNinja get an XML-RPC attack, our log analyzer module called SenseLog comes to the rescue. It detects the log lines that point to the possible attack and after a certain amount of connections, the IP gets blocked. We have filters in our service that are responsible for recognizing these suspicious lines in server logs and acting on it.














