A new flaw on the horizon!
A new flaw has been discovered in phpMyAdmin, in which an attacker has the possibility to include files on the server.
This vulnerability is caused because of a portion of a code where the pages are redirected and loaded in phpMyAdmin.
Here are the steps, how it can be achieved:
1) First, the intruder has to be authenticated, after this procedure the sql query will create a session.
2) Invoking the ../../../../../..../var/lib/sessionId the attack can be performed.
There are some exceptions though:
- $cfg['AllowArbitraryServer'] = true: attacker can specify any host he/she is already in control of, and execute arbitrary code on phpMyAdmin
- $cfg['ServerDefault'] = 0: this bypasses the login and runs the vulnerable code without any authentication.
How to be protected against it?
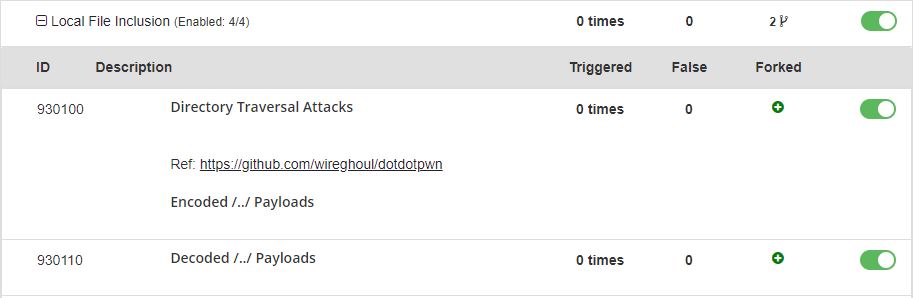
You do not have to worry, as we are thriving to make the necessary steps on zero days, you are safe and sound with BitNinja. Our WAF module has already patched this vulnerability to defend your server from this flaw, all you have to do is to enable the rule of 930100 and 930110 on the appropriate pattern ( the rules can be found under Local File Inclusion). You might try with other rules, like Remote Code Execution, Remote File Inclusion, PHP General Attacks but please be careful with these rules as they can cause false positive alarms.